Phishing, smishing, pretexting, business email compromise – welcome to the ever-growing world of social engineering attacks! As more data breaches make headlines, you may have heard of these different types of social engineering. But, unless you’re familiar with these terms, they might start to get confusing.
In this blog post, we explore these 5 common types of social engineering attacks, how they’re different from each other, and what you can do to mitigate such incidents.
firstly, what is social engineering in simple terms?
Social engineering relies on human error. Attackers manipulate and deceive users into revealing sensitive information or performing an action such as giving the hacker access to data or funds. Check out the video below for a simple explanation of social engineering or read our blog post, ‘What is Social Engineering?‘ to learn more.
5 types of social engineering attacks
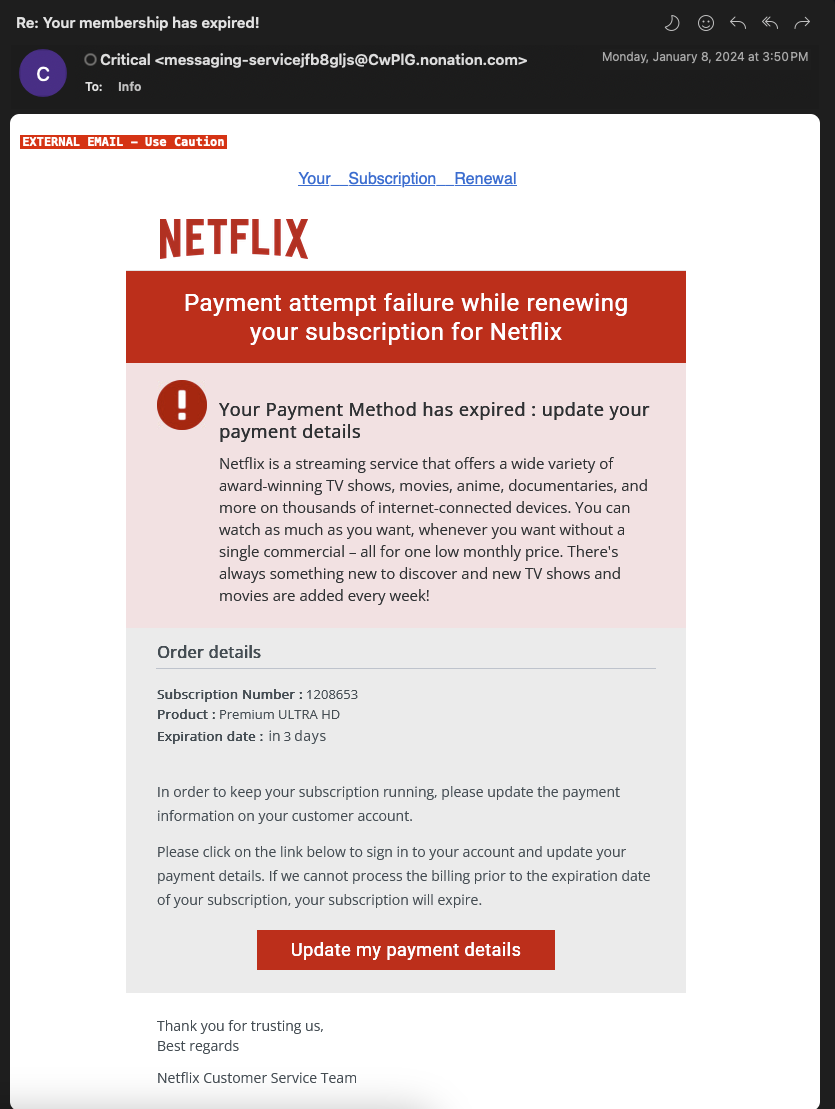
Phishing
Phishing is one of the most popular and common forms of social engineering. Hackers distribute fraudulent communication via email, SMS, or other mediums to manipulate the victim into clicking on a malicious link, downloading infected attachments, or sharing sensitive data, such as their account credentials. Hackers typically use emails for phishing with subject lines that create a sense of urgency. While phishing attempts can sometimes involve outrageous demands, a lot of hackers today are crafting more convincing messaging. For more information on phishing, check out our blog post Top 3 Red Flags of Phishing.
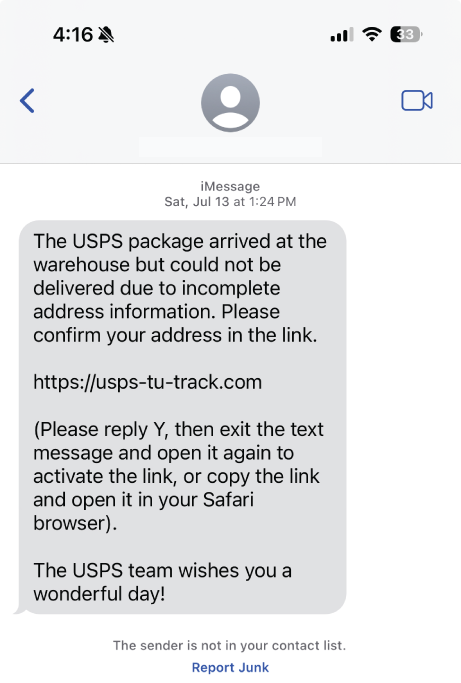
Smishing
Business email compromise (BEC)
Business email compromise is a type of spear phishing campaign where attackers send spoofed emails impersonating an organization’s CFO, CEO, or another senior executive to get your users to make wire transfers, purchase gift cards, or share confidential data.
For instance, say a new entry-level employee joins your business, they can become a target for social engineering attacks. Most people share job updates on LinkedIn and a hacker could use this information. Once they identify your company’s leadership, there are many ways for a hacker to guess your corporate email address. With all this information, the hacker may target this new employee with spoofed emails impersonating your CEO. The email messaging may create a sense of panic or urgency to get the employee to perform an action without properly looking for signs of phishing, such as an incorrect domain in the sender’s email address.
BEC attacks are a growing and costly threat to businesses. According to data from the FBI’s Internet Crime Complaint Center, BEC resulted in total losses of nearly USD 2.4 billion for victims in 2021. BEC attacks are dangerous because they do not include a malicious link or attachment, so they can go undetected by typical email security systems. You need your employees to equipped to detect and report a BEC incident.
Below is an example of a BEC of our CEO/Founder, David Gravel. This spoofed email was sent to employees in hopes that someone would fall for the scam and purchase gift cards to send to the attacker. Notice the urgency of the subject line.
Pretexting
Vishing
Attackers may pretend to be a bank official, tax authority, tech support personnel, airline official, among others, to deceive users into sharing sensitive information, such as credit card information or date of birth. Hackers may even call your employees pretending to be a known third-party vendor or event organizer with convincing scenarios to get them to perform an action.
It’s important to note that hackers have a lot of tools like voice-altering systems, fake phone numbers, or VoIP technology to create more convincing false identities.
what is the difference between phishing and pretexting?
Both phishing and pretexting attacks have a common goal, but the execution is where they differ. Phishing attacks generally use communication that creates a sense of urgency or panic to trick a user into divulging sensitive information. On the other hand, pretexting involves building trust with a user to get them to share data or provide access to systems. Further, attackers generally send out mass phishing communication hoping for some users to take the bait out of fear or haste. Pretexting, however, requires a more complex approach where attackers create research-backed narratives that appear legitimate and convincing to targeted users.
here’s what you can do to mitigate social engineering attacks
Here are two key things you should do to enhance your defenses against social engineering attacks.
Security awareness training
According to the Verizon 2024 Data Breach Investigations Report, 68% of breaches involved a non-malicious human element, like a person falling victim to a social engineering attack or making an error. This shows the importance of comprehensive employee security awareness training around social engineering. Your people are your first line of defense, so if they are not aware of such attacks then they will not be able to stop them. So, educate your employees on the different types of social engineering, how to identify the red flags of such attacks, and how to report them internally for further action.
Social engineering testing
and, before you say ‘only big businesses are a target for social engineering’ …
On average, an employee of a small business with less than 100 employees will experience 350% more social engineering attacks than an employee of a larger enterprise. A false sense of security often prevents small and medium-sized businesses (SMBs) from implementing robust security measures to mitigate cyberattacks. This belief that their business is too small to be breached is exactly the type of sentiment that makes them a target. Hackers know that many SMBs are not prepared to defend against a cybersecurity incident, which means they can steal valuable data without putting in a lot of effort. So, make sure to implement strong security protections and educate your employees about social engineering to defend your business against these attacks.
explore our social engineering testing & awareness training services
Click below to check out our social engineering testing services and security awareness training services or contact us today to get started!
Related articles
Business Email Compromise: Top BEC Tactics & How to Protect Against Them
We take a look at Business Email Compromise, including common BEC tactics and what your business can do to protect against them.
FFIEC CAT Sunset: Why the CRI Profile is a Strong Alternative
With the FFIEC CAT sunset approaching, we explore why the CRI Profile is a strong alternative to the CAT for financial institutions!
FTC Safeguards Rule Compliance for Auto Dealerships
We’ll go over the FTC Safeguards Rule, what it requires, and how a managed service provider can help auto dealerships stay compliant.